In this article, I will not be doing any practical demonstration of the vulnerability, due to different reasons. But I will share all the information that you should get about No rate limit on forgot password page, how to identify it and how to prevent it from happening.
Now, let’s dive into the article. And I am gonna explain this topic using one Hacker-one report, which is a simple report and easy to understand as well.
Now the link to the report is https://hackerone.com/reports/751604
I will be sharing some more Hacker-one report links in the last section of the article and hope you might get good information about No rate limit on forgot password.
First,
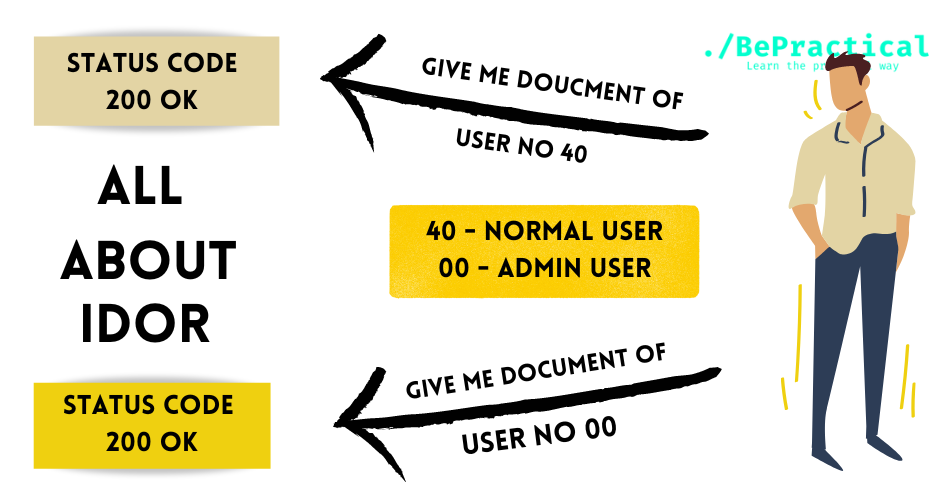
What is No Rate Limit?
- No rate limit means, every user in the internet is using Face-book, Instagram, Whats app and etc… Right .
- And the User will definitely have an IP address and that IP address should be limited, because if a user is using the application through the same IP continuously. Then it might end up crash of the server at the company side.
- So, this is also a good vulnerability to find out when it comes to finding out your first vulnerability in the real world .
Steps to reproduce the vulnerability: ( According to the report)
- Go to the password reset page of the website or the target.
- Now, Enter the email and before clicking on reset my password or continue.
- Try to intercept the request in the burp and capture it.
- Now, after capturing the request in the burp, then send it to intruder.

- Accept-Language: en-US,en;q=0.$5$ add the payload to look like this.
- It means, first when you open the intruder after sending the request to intruder
- It will automatically select some fields and show you, In the above picture, you can see all the things. first you need to do is to clear all the fields. The clear button will be in the right side of the intruder tab.
- Now bring the mouse cursor to the field which is mentioned in the 5th step and double click and click on to add
- That’s it, you had completed half of the task.
- Now, after completing this process. Now moving on to the next tab. Now it’s time to set the payloads.

- In the payloads set, you will be able to see payload set and payload type, in that change the payload type to Numbers.
- Now, in the payload options, you will see Numbers range, set the value like 1-100 and in the step value give 1 if you want to perform it for 100 times, or if you want to perform it for 50 times then give the step value as 2
It will show you different value, because I am showing it for you as an example so that you get a clear understanding of that thing.

- Now, Click on start attack.
- Boom, If you see all Status codes 200OK and if you 100 emails in your inbox.
- Then, you had discovered a rate limit vulnerability.
- And most importantly you should keep this in mind, while performing you should also check that if they had implemented any rate limit cases, means the limit up to 10000 rate limit.
- It means some companies, they implement a technique in which they keep rate limit up to 10000. So if we put 100 payloads or 9999 payloads and we got 200 status OK. But still they may not consider that as a vulnerability because they had already implemented a case where you can perform the rate limit up to a certain limit.
- If you are able to bypass the rate-limit after 10000 then it would be considered as a rate limit vulnerability.
- I am saying that this would be a case scenario, that might occur in the future.
The complete procedure is complete and I hope you had got some information regarding this vulnerability.
Then what would be the impact of this vulnerability,
Impact of this vulnerability:
If You Are Using Any Email Service Software API Or Some Tool Which Costs You For Your Email This Type Of Attack Can Result You In Financial Lose And It Can Also Slow Down Your Services It Can Take Bulk Of Storage In Sent Mail Although If Users Are Affected By This Vulnerability They Can Stop Using Your Services Which Can Lead To Business Risk
It would lead to bad reputation about that company. And Loss of money too, if they are using some sort of Email service software API.
What would be the mitigation?
- First of all, I would like to recommend to implement something like captcha solving.
- Second, Try to restrict if many request are coming from a single IP then, block the IP for sometime and then give access to them.
I hope you had got all the information about the no rate limit vulnerability on the forgot password page, how to find the vulnerability, what would be the impact and what are the mitigation should be taken.
As I mentioned I will share you some hacker one reports about this no rate limit vulnerability , the reports are mentioned below.
- https://hackerone.com/reports/751604
- https://hackerone.com/reports/838572
- https://hackerone.com/reports/903363
- https://hackerone.com/reports/774050
- https://hackerone.com/reports/77067
Thanks for reading this article, if you have any suggestions, or any questions please let us know that in the comment section.
Thank you.