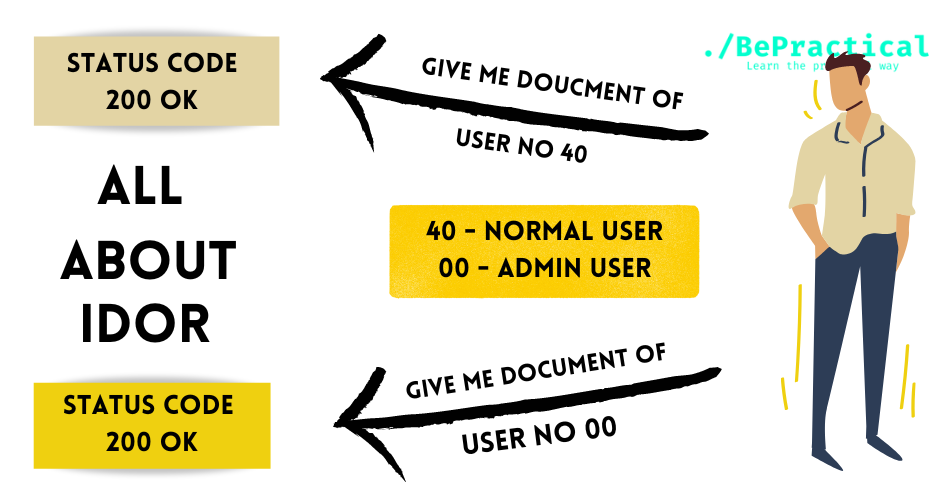
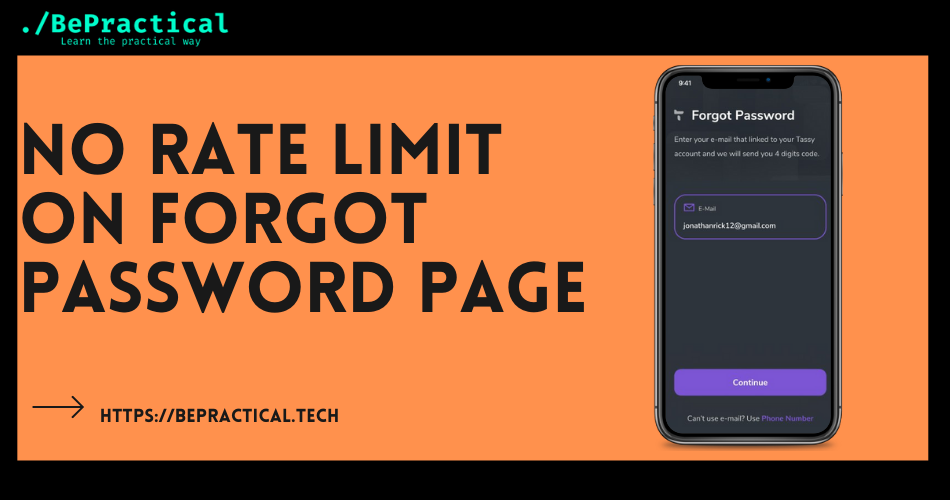
Hello everyone, today we are going to discuss about information disclosure vulnerability and it can be found on most of the web applications. But finding the vulnerability is some difficult. I will show you some examples of information disclosure vulnerability.
And we do have CSRF POC generator in our website. And the link for that is mentioned below.
CSRF POC Generator link: https://bepractical.tech/tools/csrf_poc_generator/
Now, let’s get back to the topic,
Today, I will take you through two beautiful write-ups about information disclosure, and it will not take you so much time reading this article.
I hope after reading this article, you might find you information vulnerability and that could get you a bounty, and if you get that let us know through comments.
What is information disclosure vulnerability?
Information disclosure – here we can see it in a way that,
Information – For example information about us.
Disclosure – disclosure means disclosing something that shouldn’t.
So, combining these, the information about us which shouldn’t be disclosed to anyone is leaked. This attack or this thing is known as Information disclosure vulnerability.
Now a days everything is being online, and our information is also being going to online and we don’t know that our information is safe until there is no cyber attack against where we kept our information.
How to find out these types of vulnerabilities.
This information disclosure vulnerability can be found on every website on the internet but we should look where the sensitive information is located and can it disclose the information.
we can find these using:
- Using Google Dorks
- Through GitHub à Git recon
- At the endpoints where sensitive information is
I will show you in one of this method and give you the write-up links from where you can learn about those vulnerabilities.
Now, many of you might heard about Google Dorking.
I will just summaries what is Google Dorking,
Google Dorking is a method through which we can the information which we want that are not easily available by searching using normal method. And it uses some sort of queries that help you get the information and they are also can be referred as Dorks.
Here are some of the dorks that are helpful for you finding information disclosure about the target,
Before going to the dorks, let’s understand what is a google dork. So after seeing the dorks you can get some idea about why the dork is going to be used.
Example of google dork is: site:com intext: tshirts
Here let’s split the dork into two,
- Site:com à this means get me the websites which are having .com at the last of the website.
- Example: google.com , Microsoft.com apple.com
Site:in à this means get me the websites which are having .in at the last of the website.
Examples: amazon.in, flipkart.in and etc ….
- Intext: tshirts à This referes to get me websites which ends with .com and along with bring me tshirts in the webpage.
And I will show you some other google dorks to get some idea.
Site:com à this is used to specify which website you want to get.
Intext:text à this dork can be used to get the webpage which have the text you mentioned.
Inurl:text -à this dork can be used to get me the website in which of the URL have the text mentioned
These are some basic dorks which are used and combining these dorks you can form the dork which you need.
And here are some dorks that could help to find out the information disclosure vulnerabilities.
They are mentioned below:
- “END_FILE” inurl:”/password.log” à Using this dork you can get the username and passwords.

- “Index of” inurl:phpMyAdmin à If the website is using PHP then using this dork you can find out the phpMyAdmin panel of the website.

- “Index of /wp-content/uploads/backupbuddy backup” zip à Using this dork you can find the backup zip file and get sensitive information.

These are some of the information disclosure dorks that could be used against your target. I will share a GitHub Repository in which you can get the Google Dorks that could help you.
GitHub Repository Link: https://github.com/Proviesec/google-dorks
And I wouldn’t say that you will definitely get a information disclosure of the target you are working using Google Dorking because it might be wrong, because they may already got reported about this and they might fix those.
So I am saying that you might have a chance of getting a information disclosure vulnerability.
Ok, but what could be the Impact of the vulnerability.
Impact of this vulnerability:
Ok, I hope you had got an idea how you can find some information disclosure for your target using google dorks.
The impact of this vulnerability could be,
- If the target is leaking some sensitive information about the database username, password, then it could lead to takeover of the database.
- If the target is leaking the backup files like admin_backup.zip then it might lead to takeover of the website only.
- If the website is disclosing the users’ details, then the company reputation might get down.
- And etc…
GitHub Recon:
I hope everyone know about GitHub. GitHub is a online software development platform. Using it, we can store the code, track the process of the project. And it could be easy for developers for sharing the codes.
Developers while developing the application they might leave some sensitive information and in the future that might lead to exploiting of their own website.
The developer should not leave sensitive information in the GitHub so that sensitive information of the website of theirs won’t be disclosed.
And we can find these, using some dorks known as GitHub dorks.
Before, going into Dorks, let’s see the basic dorks that could help you.
- Language:python à this will help you find the code which is written in python.
- Site:com à specifying the target on which you are going to work
And etc
And here are some examples of the dorks:
- Language:python security_credentials site:target.com
- Language:python api_key site:target.com
- Language:bash api_key site:target.com
Not only these, there are many more dorks through which you can find the vulnerability.
And I will be sharing a write-up link, which is one of my favourite write-up till date, and I hope you might get good knowledge after reading the write-up about the GitHub recon.
Write-up link: https://orwaatyat.medium.com/your-full-map-to-github-recon-and-leaks-exposure-860c37ca2c82
Sensitive endpoints which lead to information disclosure:
We can find these information disclosures at some endpoints like where the users information is getting stored.
User’s information is stored endpoints are :
- Edit Profile
- While Signup
- and etc …
At these endpoints you may get the vulnerability. And there could many more endpoints, but these two endpoints have the most information about the user.
And I guess, we came to the end of the article, and I hope you had got the information about the information disclosure vulnerability.
And I hope I had covered the things that I know, if there is anything that I had skipped, please let me know in the comments. So that I will add that into the article.
Thank You.