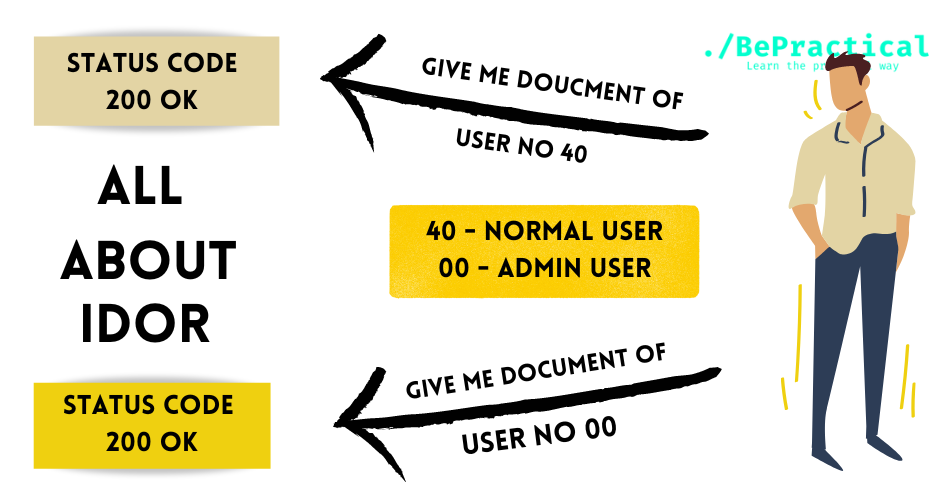
What is XSS? (Cross-site scripting)
- Cross site scripting is also known as XSS. And it is the most common vulnerability which is identified in the most live web-based applications. The web application is the collection of user inputs and search fields. So this is the reason which Cross-site scripting happens.
- In the user input, malicious JavaScript code is inputted by the attacker or hacker, which aims to steal user sessions or do cruel code executions.
What are the types of cross site scripting or XSS
- Reflected XSS: Reflected XSS vulnerability occurs when a malicious script is reflected in the website’s result or response.
- Stored XSS: The malicious data is stored permanently on a database and it is later accessed and run by the victims without knowing the attack.
- DOM XSS: DOM based XSS is where in the attacker’s payload is executed due to modifying the DOM environment in the victim’s browser used by the original client side script. The client side code runs in an “unexpected” Manner
Above those are the types of XSS or Cross site scripting. More importantly we are going to discuss about the Reflected XSS today.
Reflected XSS:
- Reflected XSS is a type of vulnerability which is found on most of the websites, now a days. This happens when the given user input is not properly validated by the server and then this vulnerability is present.
- Reflected Cross site scripting is the type in which the injected script is reflected of the web server, like the error message, search result or any other response. Reflected type attacks are delivered to victim’s or targets via another path such as email messages or phishing. When the user is tricked into clicking the malicious script or link, then this attack triggers the user’s browser.
A simple example to find Reflected XSS is the search field.
- A website have a search field for searching items or searching for some information and it starts from there.
- We will add the input to the search field. If the search input is not validating the user input then it may produce the Reflected XSS vulnerability.

Example of attacker stealing private data using XSS
Steps of attacker stealing private data using XSS:
- The attacker sends a link that contains malicious JavaScript code.
- The Malicious link is executed for normal users at his side on any browser.
- After execution, the sensitive data like cookies or session ID is sent back to the attackers server and the normal user private data is compromised.
- The normal user will not know about this issue.
Examples of Reflected XSS that happens via Search Parameter:
- Consider a web application that takes search string from the user via the search parameter provided on the query string:
https://www.example.com/test.html?search=bepratical
- The web application will the show the search value which is provided by the user on the HTML page.
- Check how the input is properly validated by the server and if the server is not validating the input given by the user.
- Then try to inject the payload for getting the Reflected XSS.
- A basic XSS payload is : <script> alert(1) </script>
- Now inject the payload in the search parameter in the web application and see the response.
- If the payload is executed then it is vulnerable to Reflected XSS.
Example for finding an Reflected XSS: ( I am using testphp.vulnweb.com for testing purpose)
- Open the website. Now type something like bepractical search for reflections.

- Now you can see that you are able to see bepractical on the website. Now try to inject the malicious script or payload into the search field.
Payload : <script> alert(1) </script>

- Now when we click on go you may the result. If the website is vulnerable you can get the vulnerability.

- As you can we get a Pop-Up alert saying 1.
- So it is vulnerable to Reflected XSS.
Impact of Reflected XSS:
- The attacker can hijack user accounts.
- An attacker could steal credentials.
- An attacker could ex-filtrate sensitive data.
- An attacker can steal cookies and Session ID.
- An attacker can quickly obtain access to your other client’s computers
How to overcome the problem of Reflected XSS:
- Try to user browser technologies that do not allow client side scripting in input fields or URLs.
- Make sure that all the user-supplied inputs are adequately validated before sending them to the server.
- Try to implement a WAF for blocking while testing for these kind of vulnerabilities.
Some Hacker One reports of Reflected XSS:
- https://hackerone.com/reports/846338
- https://hackerone.com/reports/697099
- https://hackerone.com/reports/340431
- https://hackerone.com/reports/840759
- https://hackerone.com/reports/1350887
Conclusion:
So, I hope you had understood about the Reflected XSS and the damage it could costs against the web application.
So there are two main points to remember:
- Always validate the user given input.
- Try to implement a WAF to block some of these types of vulnerabilities.