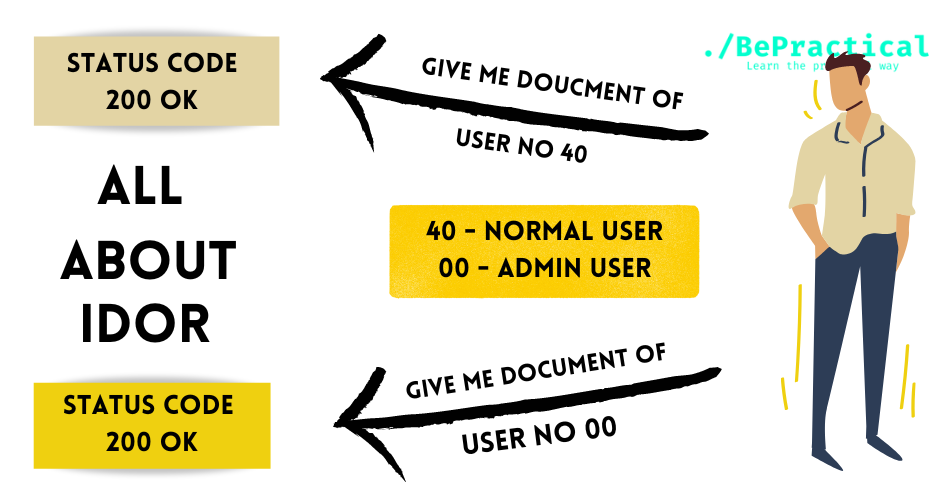
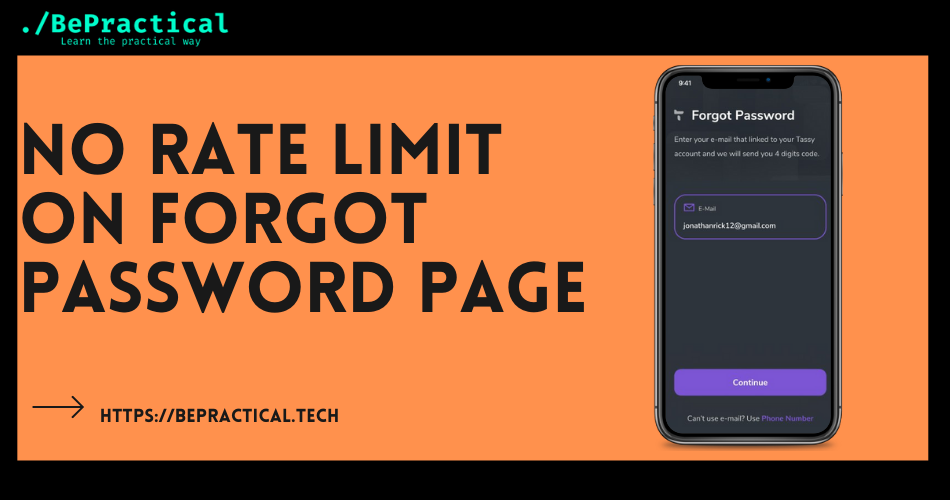
What is XSS? (Cross-site scripting) What are the types of cross site scripting or XSS Above those are the types of XSS or Cross site…

- 1
- 2
- 3
- 4
- Next Page »